
|
Digital Choke Daynotes  |
|---|
| Daynotes | a daily journal of our activity | |
| Digital Choke | an action that is sometimes needed for your computer; also a short techno-story available here. |
| "Daynotes" are popularized by a Internet Web site called the "Daynotes Gang" (http://www.daynotes.com or http://www.daynotes.org), a collection of the daily technical and personal observations from the famous and others. That group started on September 29, 1999, and has grown to an interesting collection of individuals. Readers are invited and encouraged to visit those sites for other interesting daily journals. You can send your comments to us by clicking on any mailbox icon. | Reports |
"There is nothing to see here." -- Zork I
It was a busy weekend. Saturday morning started out with a visit from the DirecTV installer, who installed the new dish and set up the receivers. Pam went off to the local garage sales, but at her first stop (just a block away), the car wouldn't start. So she walked back to the house. That may have saved a bit of money at the garage sales, but it was more than offset by the cost of a new battery. I was able to get one more start out of the battery, so drove over to the local parts store, grabbed a new battery (yes, I paid for it), and quickly installed it while in front of the store.
By that time, it was noon, and time for fun time with the grandchildren. So it was off to the county fair in Yuba City/Marysvale (about 40 miles NE of Sacramento, in the lower Sierra Nevada mountains. It's a real nice, low-key, small county fair. The fairgrounds are nestled among tall pine trees, and there are the usual areas. The kids liked the animal areas: we went to the petting zoo, where the big hit was the baby pigs, then to the small animal bars for the sheep, goats, horses, etc. Much petting was involved. There was the food area, with corn dogs and frozen lemonade, giant cinnamon buns, and all the other junk food on a stick. The grandchildren are 3 and 1 1/2, so the carnival area didn't have much for them there. But there was a toddler play area sponsored by a local pre-school which was a big hit. They had a small table with lots of bird seed and containers and scoopers, and some small picnic tables for coloring fans (paper plates on a possible stick), and some small riding toys. We spent quite a bit of time there. It was relaxing, and it didn't cost anything (although we made a small donation to the pre-school).
Saturday evening was spent watching kid videos and movies, playing with puzzles, and pizza delivered to our door. (Pizza delivery is a new thing for us; in our previous house, we didn't live in a pizza delivery area.) By the time we got the kids to bed, it was a bit late for posting.
Sunday was spent taking care of the grandkids, and keeping them entertained. Their parents got back from their 'mini-moon' in time for dinner, which was a prime-rib from Sam's Club that turned out real well. We all had a nice visit, including a call from the youngest daughter who is in college in Idaho.
So we wake up this morning, and the news tells about a dumpster fire in back of some apartments downtown. And the address is really near where our son lives. Someone set the dumpster on fire, and the fire spread to a couple of palm trees on the alley, along with four cars that were totally destroyed. We hadn't heard from Jason, so we figured all was well. We drove by his apartment on the way to work, and luckily saw that his car (actually, my truck, since his car is in the shop to replace the transmission again) was not among the burned-out hulks in back of the apartment.
We talked to him later, and he said that although the fire department didn't have them evacuate, he had quickly gotten his computers and music instruments ready to take out of the apartment just in case. (He uses his computer and keyboard and other stuff to compose music and work on self-made videos.) He usually parks in back of the apartment, but last night his usual spot was taken, so he parked out in front of the apartment on the street. That was lucky for him, since the car that took his spot was among those that got burned. And it was lucky for us, since we had just lately paid off the truck (a 1994 Ranger) and reduced the insurance to the minimum, so we weren't covered for fire damage.
So, it's been an exciting weekend. And now your are up to date. Speaking of that: make sure you have your patches installed. "MBlast" is out to get you. You know the drill, and the 'mantra'.
I spent part of the day ensuring protection from the MSBlast worm. We had previously protected our network from this type of attack by blocking those ports at the border. And we ensured that our public-facing servers had the correct patches.
At home, I had already spent some time installing all the updates and patches. And I had advised others in my family to get current. Not so lots of other people. Although the technical reports are that this one has a few bugs in it, the next one might not be so buggy. So, the mantra still holds.
Other than that little bit of excitement, I spent the rest of the day learning a few things for another big project, and catching up on others. Not too exciting, but a productive day.
More news and info about the Blaster/LoveSAN Internet worm. I sent this message to Jerry Pournelle, who published it on his site here (he gets a few more readers than I do):
As expected, the "Blaster" (aka "MSBlast" and "LoveSAN") worm has new variants that are a bit more efficient, and have different names for the executable program that is installed on the computer. These new variants are not damaging to files on your computer, but the potential is there. It would be quite easy for a Blaster clone to contain a simple command to format your hard drive or delete files, etc.
So it is quite important for your readers to ensure that they have protection against this worm. They need to apply the Microsoft patches to be protected. Note that the worm doesn't arrive in an email message, so anti-virus protection, or not opening attachments, doesn't protect your computer.
A firewall of some sort will help (there are reports that the XP Firewall can help), as long as the user doesn't inadvertently allow access to the worm.
The 'mantra' will help: "update patches, update virus definitions, don't open attachments"; repeat three times....
I highlighted an important statement in that message. The vulnerability allows the attacker to run any program on your computer, without your knowledge. Here's the explanation of how it works (from the Network Associates site, full info here):
This worm spreads by exploiting a recent vulnerability in Microsoft Windows. The worm scans the local class C subnet, or other random subnets, on port 135. Discovered systems are targeted. Exploit code is sent to those systems, instructing them to download and execute the file MSBLAST.EXE from a remote system via TFTP.
The worm contains a payload to initiate a Denial of Service attack against windowsupdate.com after August 16. This payload involves sending SYN packets to windowsupdate.com on TCP port 80 for the purpose of preventing users from patching their systems via Windows Update.
Computers that have up-to-date antivirus software will detect the worm executable (msblast.exe) upon download and prevent that machine from becoming a host for W32/Lovsan.
However, unless the system has been (MS03-026) patched, it is susceptible to the buffer overflow attack from an infected host machine. An infected machine (running msblast.exe) will send out malformed packets across the local subnet to the RPC service running on port 135. When these packets are received by any unpatched system, it will create a buffer overflow and crash the RPC service on that system. All this can occur without the worm actually being on the machine. This means that the remote shell will still get created on TCP port 4444, and the system may unexpectedly crash upon receiving malformed exploit code.
Other symptoms may include:
- inability to cut/paste
- inability to move icons
- Add/Remove Programs list empty
- dll errors in most Microsoft Office programs
- generally slow, or unresponsive system performance
By applying the MS03-026 patch to the machine, it will prevent the RPC service from failing, in-turn solving these symptoms. It is very important that the machine is rebooted after the patch has been installed. The machine can then be updated to the latest dats/engine/config and an on-demand scan run to pickup msblast.exe, IF it exists. All of these symptoms are related to the RPC vulnerability and not necessarily due to W32/Lovsan running locally. Msblast.exe may not be present at all.
Network Associates updated their virus definitions today (Wed), so the worm's action of downloading the file might be caught. But that depends on the anti-virus settings; you have to enable that download detection. The number of infected computers is estimated between 250,000 and 750,000 (as of Wednesday night), although those numbers may be "WAG's". You might find some current numbers at the Internet Storm Center run by SANS (here), with technical details about the worm here. And this graph shows the increase in the port 135 port scans.
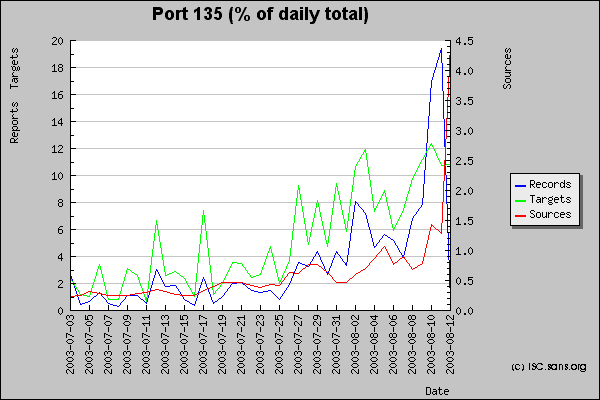
Microsoft has some specific instructions about this worm, here, for less technical users. Network administrators should read this. Your network administrator should already know about this worm. If they don't, they should be replaced. (And probably smacked upside their head.)
Be aware that there is a very high probability that additional variants (besides the two already known) will be launched.
Update, Patch, Protect. Update, Patch, Protect. Update, Patch, Protect. What I tell you three times is true.
Let's start off this early post with one of the best set of instructions on how to remove (or detect then remove) the Blaster worm. It's courtesy of the guys at CERT, and is here. It is very thorough, and includes links to other information (such as how to enable the Windows XP firewall). The CERT site is very good for all sorts of security information. And you should subscribe to their excellent mailing lists for security notifications.
Another good source for security information is the SANS site (their main page is about all of their training seminars; look for the links at the top of the page for other content). The 'reading room' contains many articles on all sorts of info security subjects. They also have some good mailings about computer security. For instance, today's newsletter included an editorial comment from the SANS group about the Blaster worm:
About the W32/Blaster worm: Yeah, it was painful, but it could have been
worse. That is, unless you allow arbitrary TFTP traffic to pass through
your network and gateways.Come on folks, this is not a well-written worm. Its method of scanning
for new hosts is slow and not as effective as it could be. It requires
not only port 135 access but also port 69 (TFTP) access. Just imagine
if the worm pulled everything in over the established connection (rather
than using TFTP) and it was more efficient at scanning. If you think
the current incarnation was a nightmare....One common situation popped up often enough that we feel it important
to comment. Many folks [network admins - ed.] locked down their gateways and checked their perimeter servers for vulnerability. Satisfied that nothing could come in from the Internet, they were humbled when an internal employee
brought in an infected laptop from home. Sure, the servers were OK, but
the desktops proved to be a fertile worm incubation playground.Moral to the story: Security doesn't stop at the perimeter. From the
mightiest of servers to the lowliest of desktops, and all print servers
in-between, everything needs to be patched when dealing with a
nondiscriminatory worm.
There is some important concepts in there (I highlighted it in red). You need to have 'defense in depth'. Network admins can't rely on 'border' protection (bring your infected laptop into your work network; now your work network is infected). Home users can't rely on their firewalls (bring your infected laptop home and hook it into your home network, and your home network will be infected).
And while you Linux-boosters might start chortling about how insecure Windows is, they should see this article (among others found via Google News). It seems that
The Free Software Foundation, sponsors of the GNU free software project, said Wednesday that a key server housing the group's Linux software was broken into by a malicious hacker.
This took place back in March, and is just getting some wider publicity. The hack took advantage of a vulnerability in the Linux FTP (file transfer protocol) process, and was able to get into their main FTP server where all the Linux programmers get (and store) their code. So:
All the same, the FSF encourages GNU users who downloaded software from the site between March and July, as well as Internet sites that mirror the source code from the compromised server to verify the integrity of their GNU software.
The "mantra" applies to everyone.
"There is nothing to see here." -- Zork I
"There is nothing to see here." -- Zork I
|
Copyright (c) 2000-2003
Two Bridges Group,
All Rights Reserved |
|
Digital Choke Daynotes  |
|---|
|
|