Digital Choke Daynotes |
What's a Daynote?"Daynotes" are daily (usually) journal entries of interesting happening and discussions. They are not 'blogs', which are often just a collection of links to other information (although we do include links occasionally). Daynotes are much more interesting (we hope). These "Digital Choke Daynotes" were inspired by the collection of daily journals of the "Daynotes Gang" (see sites at .com, .net), a collection of daily technical and personal observations from the famous and others. That group started on September 29, 1999, and has grown to an interesting collection of individuals. Readers are invited and encouraged to visit those sites for other interesting daily journals. If you have comments, send us an email. A bit more about me is here. You might also enjoy our little story about the death of the 'net. |
Reports
|
A busy weekend; well, it started out that way, then got quiet.
Saturday morning was a maintenance window for computer systems at work, so we took the opportunity to upgrade our mail filtering server (SurfControl eMail Filter) to the current version. We have two mail servers, with a third server holding the SQL database for the mail server.
So we started out with installing all the latest Microsoft patches, backup up some important configuration settings, and then applying the update. No problems with either update (Microsoft or SurfControl). We made sure that mail was flowing properly, enabled some of the newer and more efficient rules, and we were done by a bit after lunch.
While I was gone, Pam and Stacy decided (well, Stacy decided) to purchase some more bedding flowers for the back yard. And to further confuse me, they actually planted them! That was a nice surprise; as you two regular readers might remember, my last flower bed upgrade caused significant muscle aches and pains for several days afterwards.
The flowers looked good, all that was needed was to enhance the drip irrigation system for the new flowers. I found some drip tubing: the "drippers" are built into the 1/4" flexible drip tube. So all that was needed was to snake the drip tubing around the rows of flowers, hook it up to the supply line, and use some metal U-shaped wires to hold everything in place.
Then I applied five bags of small bark mulch around the new plantings, and gave everyone a nice soak. Looks pretty good.
Saturday night was quiet, as was Sunday. The grandkids couldn't come by for their regular Sunday dinner visit, so things were really quiet around the house on Sunday. Pam didn't have to do a big dinner preparation (which she enjoys); we just put some hamburgers on the grill, some corn on the cob in the boiling water, and a fresh fruit salad.
I did check the mail system a couple of times over the weekend, and all was working well.
This morning, I did another check of the mail system. And found that our spam catching statistics are much increased. Before the upgrade, we were catching about 30% of all our mail as spam/offensive mail. This mornings stats (which were against the weekend's mail, which is going to be a lot of spam since we aren't open on weekend) were catching about 65% of all mail as spam.
A new statistic with this new version is a count of all refused mail connections. Since we enable "Real Time Blocking", every incoming mail is checked against the RBL sources. If RBL says it's a spam source, we deny the mail. We've had that before, but now we have stats that show we are blocking about 65% of all incoming mail because the mail is from an RBL source.
Although we'll continue to monitor the stats, it looks like the upgrade, along with the new blocking rules, will be able to block even more of spam/offensive mail. I have a couple of users here that regularly send me their spam that gets through the filters; a good test of the new rules will be if they send me less of their spam (because they are getting less spam).
Another task this last maintenance weekend here at work was to do some major reconfiguration of our firewalls. That was a bit more complex, but seemed to be successful. But the Monday morning load caused some hardware failures of the switches, with the result of decreased (or almost none) Internet access.
Now, if you want to irritate your users, then take away their Internet access. Never mind that most of that access has nothing to do with their work. But they do complain when it's not there. Our firewall team got things working a bit after lunch. Just in time for the big spike in use because of the Michael Jackson verdict. It will be interesting to run some reports of web usage comparing today's access with a similar time period last week. I get to monitor our web filtering process, and I see a lot of apparent non-business use of the Interweb.
Richard M. noticed the incorrect date at the top of this page (now corrected). I'm sticking with the story that it was a typo.
He used the mail form we use here for reader comments. He asked for my email address (which I gladly gave to him privately), saying that he found that to be a bit more convenient than mail forms. And that's a reasonable request.
But I use mail forms to prevent 'mail harvesting'. Just like Google wanders through the "Interweb', mail harvesting programs wander through a web site looking for mail addresses on the web pages. These types of programs are used by spammers to gather valid email addresses. And they are quite efficient.
I ran a 'mail spider' against our public web site at work. And it found over 400 unique email addresses. The process took under 10 minutes. So you can see that a mail spider can be quite a good tool for a spammer to use, as it gets 'real' email addresses.
As an experiment earlier this year, I did a test of a new email address I created for this site. As the two regular readers here would tell you, I send security alerts to Jerry Pournelle's "Chaos Manor" web site. (Dr. Pournelle is one of the "Daynotes Gang", and has been publishing a web log/diary for a very long time, in addition to his columns at Byte Magazine, and his many science fiction books.) His site is widely read; he gets many thousands of readers every day.
So in one of my security alerts to him, I used that brand new email address. It was just part of my signature block, which he published on his site. I never used that email address in any correspondence or on any web site. It was just a one-time address.
Less than a month later, I started to receive spam mail to that email address. And I still get mail to that email address today.
So, around here, we use a mail form. You won't find the email address it uses on any web page here. Which I think is a good practice for any web site. By using a mail form rather than an email address, you reduce the chance that a mail spider will harvest those email addresses. And that will help reduce spam to your users.
I sent this off to Dr. Jerry Pournelle, who sometimes publishes my security alerts. (He has a few more readers than me.)
Reports from the security centers at USA, UK, Canada, and Australia indicate a significant increase in highly targeted emails containing malware (viruses, worms, trojan horse programs). They appear to be more successful than the 'average' malware due to clever social engineering techniques. Current software/firewall protections may not protect against this malware.
These emails seem to be very targeted. The "From" address is spoofed (faked) making it appear to be from someone you know. The subject line and text look like information related to your work (it may be copied from previous legitimate email). And the attached file appear relevant to your work.
If you open the attachment, a Trojan will be installed on your computer. That trojan can do the usual things: gather confidential information from your computer, send spam email, delete files, or use the computer for a Denial of Service attack.
The technique may also be related to the trojan-based economic/industrial espionage case that was exposed in Israel this (last?) month. And since these are highly targeted attacks, current anti-virus or firewall protection may not be enough protection. In fact, there may not be any completely effective mitigation against these attacks, even at the corporate level.
So, the most effective technique is "BDAC"-based (Between Desk And Chair). Users should (continually) be educated against clicking on links in email, opening attachments, and ensure that all operating system, application, and virus updates are applied. Spyware detection / scanning is also helpful (Spybot Search & Destroy, Ad-Aware, Microsoft Anti-Spyware -- all free). (Repeat this paragraph three times...what I tell you three times is true.)
Note also that the new Microsoft Update site will now scan for MS-Office applications ( http://windowsupdate.microsoft.com/ ). Corporate/business users should investigate the new Windows Software Update Server (free) for proactive managed automatic updates of corporate workstations (strongly recommended).
More info on these latest email threats here:
http://www.ocipep.gc.ca/opsprods/info_notes/IN05-001_e.asp (Australia)
http://www.uniras.gov.uk/niscc/docs/ttea.pdf (UK)
http://isc.sans.org/diary.php?date=2005-06-16 (USA).
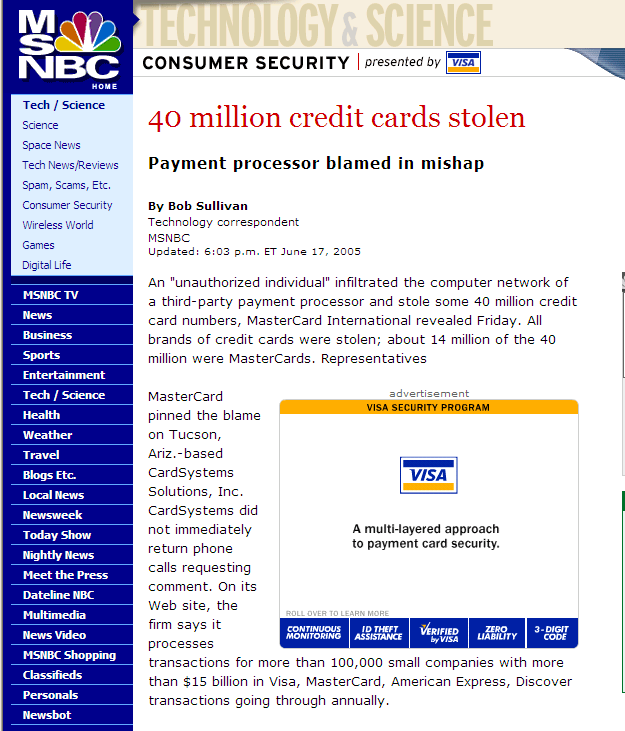
Another day, another credit card account theft. <sigh> This one involves 40 million credit card accounts. Link is here, or your favorite news site.
'An "unauthorized individual" infiltrated the computer network of a third-party payment processor and stole some 40 million credit card numbers, MasterCard International revealed Friday. All brands of credit cards were stolen; about 14 million of the 40 million were MasterCards.'
To paraphrase credit card ad slogans: "There are some things money can't buy. But you can buy a MasterCard." and "What's in My Wallet? Your Credit Card?" (Got any more suggestions? -- send them to me via the mail form.)
Side note: when I went to that news page, the advertisement I got was from Visa, talking about their "multi-layered approach to payment card security". I've got a screen capture on my site here: http://digitalchoke.com/daynotes/2005/2005-06-12.php#friday . That news page heading shows "Consumer Security presented by Visa". Heh. Here's the screen capture of that; click on the picture for a larger image.
As I've mentioned before: you should carefully monitor your credit card activity. Use your bank's web site (but type in the web address, don't click on links in emails) or ATM statements to see your credit/ATM/bank activity. In the US, get a free credit report (except NE USA states; they get free ones starting Sept 1) via here (be cautious about all other 'free credit report' sites .. they aren't really free).
And never click on email links asking you to "verify your account". They are always bogus.
... more later ...
|
||||||
|
Visitors
| ||||||